Documentation FreeFirewall
Introduction
Free firewall is a full-featured professional firewall that protects against the threats of the Internet. Control every program on your computer by permit or deny access to the Internet. Free firewall notifies you when applications want to access the Internet in the background without your knowledge.
Use cases
Monitoring and control
Monitor the Internet access of any program running on your computer. Define rules that control Internet access individually for each program.
Protection against attackers
The software protects you against attackers from the Internet and the local network.
Privacy
When surfing the Internet you leave many traces. Various techniques can be used to track internet users and monitor their activities. The software protects you from tracking and monitoring on the Internet.
Setup
To set up the software on your computer, you must first download the installation file. You can find this on the website: FreeFirewall Download.
Once you have downloaded the installation file, start it.
After the installation is completed, a shortcut appears on your desktop. Start the software.
User interface
After starting the application, the user interface of the software appears.
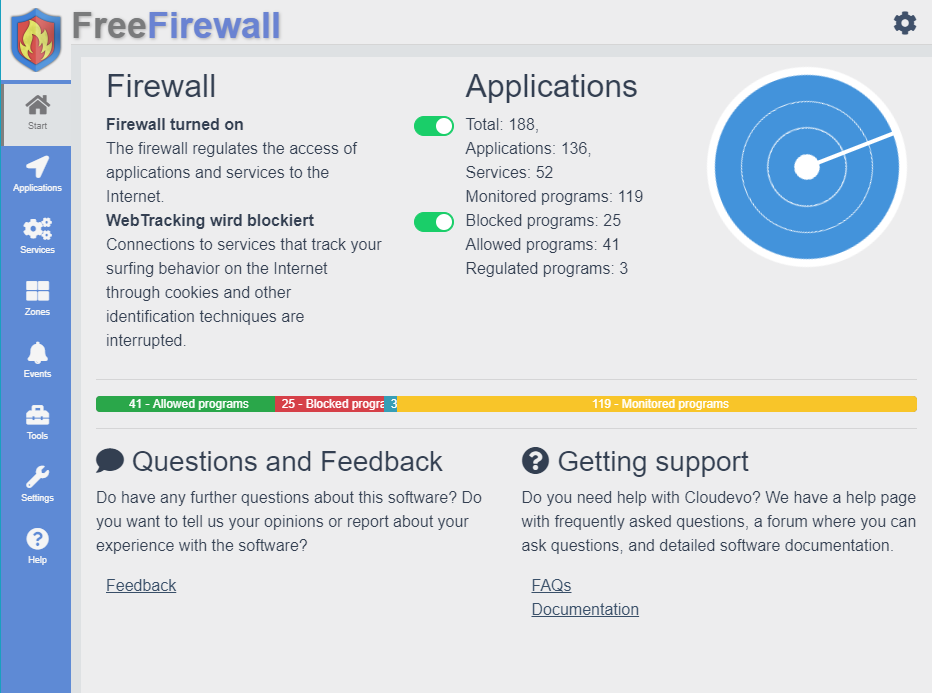
Updating the software
The software occasionally receives updates that provide new features or fix bugs.. You can check on the product page of the software whether a newer version is available or when an update appears. For each new program version, the change log is used to determine whether it is downwards compatible with the previous version. Ensure that you are installing only updates that are backward compatible with your installed program version. Each update has its own stability label:
- Beta: These program versions are still under development and have not been adequately tested. You should only install these program versions on a test device which you do not use productively.
- Preview: These program versions have not yet been adequately tested. You should only install these program versions on a test device which you do not use productively.
- Release: These program versions have been adequately tested and can be used on productive systems.
Incompatible updates
If you want to install a newer version of the program, which is not backward compatible with the existing one, you should do this as follows:
- Back up all your data from the existing installation to a secure disk.
- Note the configuration and settings of the existing installation.
- Uninstall the old program version. When uninstalling, select the complete uninstallation.
- Install the update.
- Configure the new installation with the recorded settings.
- Copy your old data to the cloud drive or to the synchronizing folder.
Update from version 1 to 2
If you want to upgrade from version 1 to 2, please follow the instructions in the section below: Incompatible updates
Uninstallation
Die Software kann mit Hilfe eines Assistenten auch deinstalliert werden. Die Deinstallation der Software kann auf zwei Wegen durchgeführt werden.
Deinstallation über die Systemsteuerung:
- Öffnen Sie das Startmenü von Windows.
- Tippen Sie das Wort [Systemsteuerung] ein.
- Öffnen Sie die [Systemsteuerung] und klicken Sie auf den Menüpunkt [Programme deinstallieren].
- Suchen Sie in der Liste nach einem Eintrag der Software.
- Klicken Sie den Eintrag der Software mit der rechten Maustaste an.
- Im erscheinenden Menü klicken Sie bitte auf [Deinstallieren].
- Es öffnet sich ein Assistent, um die Software zu deinstallieren.
- Befolgen Sie die Anweisungen im Assistenten, um die Software zu deinstallieren.
Deinstallation über den Assistenten:
- Öffnen Sie den Datei-Explorer von Windows.
- Navigieren Sie zum Installationspfad der Software. Path: C:\Program Files\Evorim\SoftwareName
- Im Verzeichnis befindet sich eine Datei mit folgendem Namen: uninstall.exe
- Klicken Sie doppelt und die Datei, um den Assistent zu starten.
- Es öffnet sich ein Assistent, um die Software zu deinstallieren.
- Befolgen Sie die Anweisungen im Assistenten, um die Software zu deinstallieren.
Ablauf der Deinstallation:
- Der Assistent führt Sie durch die Deinstallation.
- Bestätigen Sie am Ende die Durchführung eines Computer-Neustarts.
Applications
After setting up and starting the software, all running programs are displayed in the user interface.
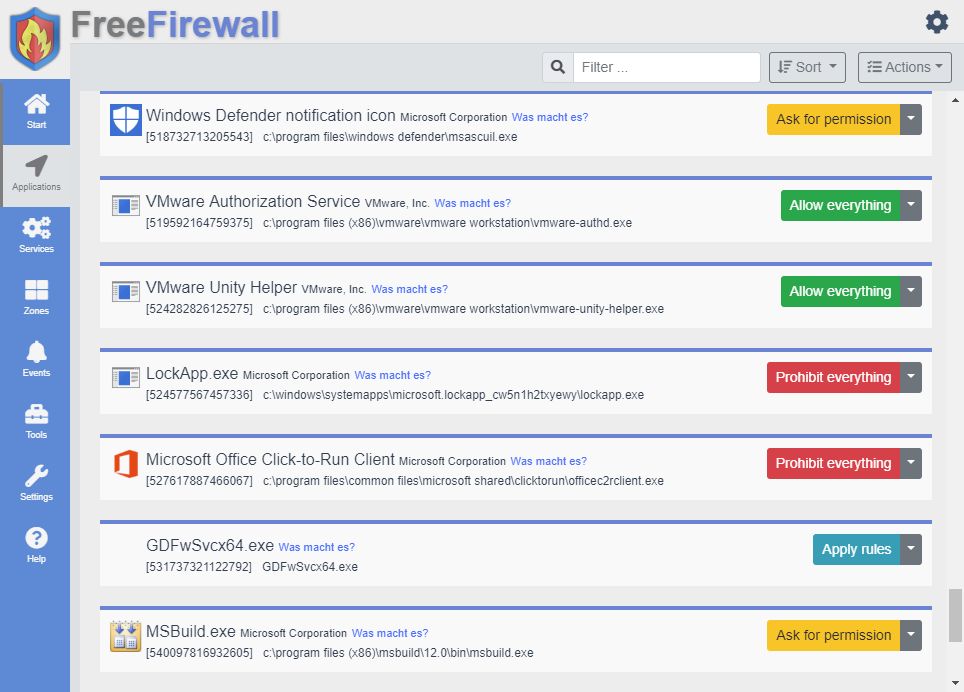
Permissions
You can set permissions for each program individually.
Possible permissions are :
- Ask for permission : Each time you access the Internet, the software displays an Internet access event that you approve or block.
- Allow all : Every internet access is automatically approved by the firewall.
- Deny all : Any Internet access is automatically blocked by the firewall.
- Apply rules : Each Internet access is automatically decided on the basis of rules for this program. Rules can be created by the user.
Services
Similar to running programs, background services are also monitored. Individual authorizations can also be assigned for services.
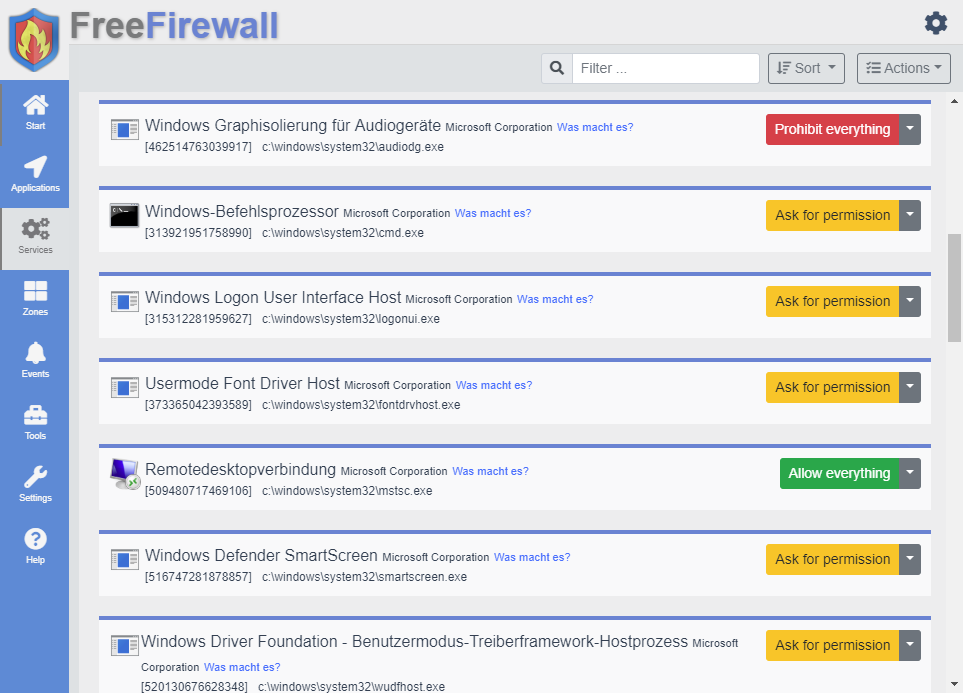
Rules
In addition to allowing or prohibiting everything from two privilege levels, there is a more precise assignment of permissions by rules. Rules consist of an address and a port and an permission.
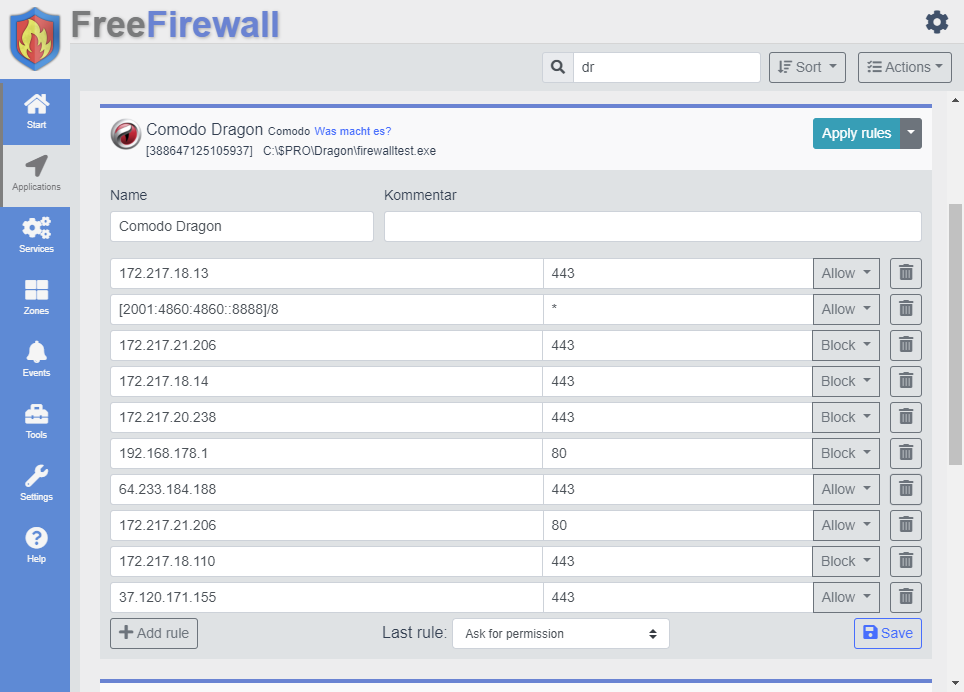
If a program accesses the network or the Internet, all the rules listed are checked until one matches the destination address. If a matching destination address is found, the respective permissions assigned to the rule are applied and processing ends.
If none of the specified rules match the destination address, the last rule will be applied. The last rule can have the following values:
- Ask for permission : If no match is found after the above rules have been processed, the software displays an Internet access event that you approve or block.
- Allow all : If no match was found after completing the above rules, Internet access is automatically approved by the firewall.
- Deny all : If no match was found after the above rules have been processed, Internet access is automatically blocked by the firewall.
- Apply selected zone rules : If no match was found after processing the above rules, then rules of the selected zone are checked until a match is found.
Add rules
New rules for a program can be created using the Add-button. A rule consists of the following parameters:
- IP address or domain name
- Port, port range or star
- Rule action
IP address or domain name : IP address can be entered in the form of an IP v4 or IP v6 address. The address may additionally contain a sub-mask in the form of a prefix length.
Examples : IP address or domain name
- 192.168.2.77
- 192.168.2.77/18
- 192.168.2.77/18
- [2001:0db8:0000:08d3:0000:8a2e:0070:7344]
- [2001:0db8:0000::7344]
- [2001:0db8:0000::7344]/64
- exampledomain.com
- subdomain.example.com
Port, port range or star : The port parameter of a rule can be specified in many ways. Either as a simple numeric number, as a port range, or as an enumeration of ports separated by a comma. The star parameter is used if the rule is to apply to all ports.
Examples : Port
- 80
- 433
- 80-433
- 80,433,8080,8443
- *
Rule action : The rule action determines if the rule applies to a network access that either blocks or allows network access.
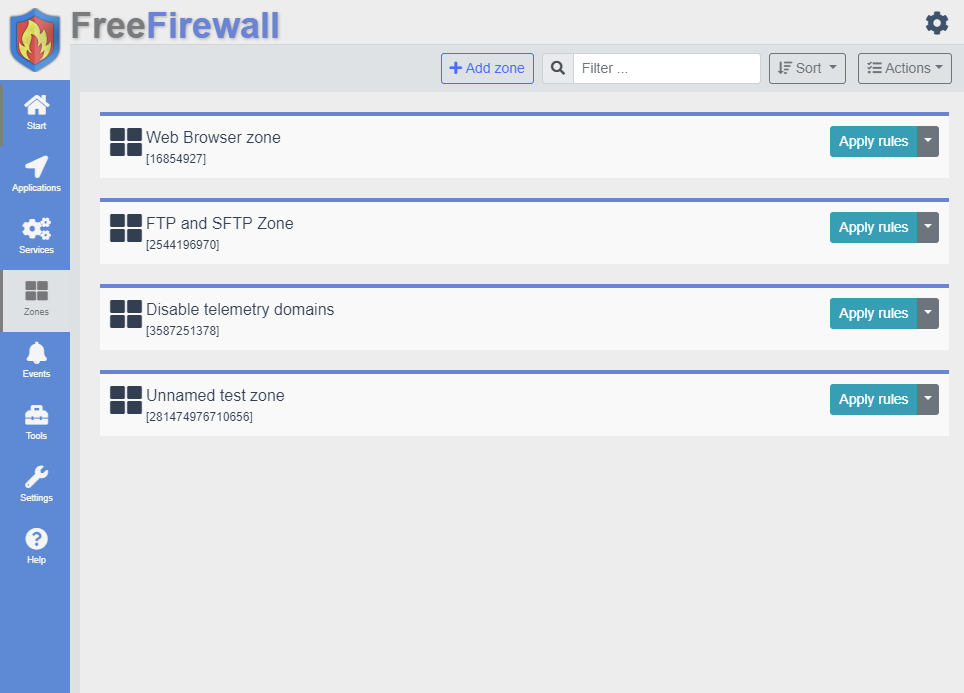
Zones
Zones are an extension of the rule concept. Rules provide a fine-grained assignment of permissions to a particular program. Since many programs should have similar permissions, it makes sense not to assign these rules individually to each program, but to create a zone. In this zone all rules are listed. Then the zone can be assigned to one or more programs.
Settings
The software provides you with options and settings to change the behavior of the software.
General settings
Start program with Windows
The program starts automatically each time you start the computer.
Check for updates and notify
The program automatically searches for a more recent version of the program and notifies you of an update.
Prevent hibernate during synchronization
While files are synchronized with the Cloud, hibernation or standby is prevented.
Language selection
Choose your language by clicking on a flag .
Synchronisation
Cloud Assignment Strategy
An allocation strategy specifies the order in which the storage space of the cloud services is been allocated.
- Optimized for speed : Combination of cloud service for maximum speed
- Random : Files are uploaded randomly to a cloud service
- Strong fragmentation : Large files are distributed to as many different cloud stores as possible
- Available disk space : Cloud services with a largest available storage space will be filled first
- Linear : Upload are distributed in the same order to the cloud storage services as they are arranged in the list
- Uniform allocation : All cloud storage services have approximately the same amount of data
Path for the cache
An allocation strategy specifies the order in which the storage space of the cloud services is been allocated.
Compression
Files can be compressed before uploading to the cloud to save storage space and transmission time.
- No compression : Files are uploaded without compression
- Fast compression : Files compressed quickly
- Medium compression : Files are compressed balanced
- Strong compression : All files are highly compressed before upload
Upload / download bandwidth restriction
Limit the bandwidth available for downloading or uploading the files. Enter a number to enable the restriction.
Proxy in company or home network
If you use a proxy to connect to the Internet, the software allows you to configure the proxy connection. The software supports different proxies:
- HTTP proxy
- HTTPS/SSL proxy
- SOCKS v4 proxy
- SOCKS v4 type A proxy
- SOCKS v5 proxy
- SOCKS v5 type H proxy
You can use the system's proxy configuration to manage the settings for all programs centrally. To do this, choose the entry in the selection menu.
FAQs
Often, the same questions are asked repeatedly. At this point we want to give you the most common answers.
Should I disable the Windows Firewall or Defender Firewall?
No. Our firewall works independently and in parallel to other products. You do not have to disable the Windows Firewall or the Defender Firewall.
Wie kann ich das Passwort der Firewall zurücksetzen?
Das Passwort der Firewall kann auf zwei Arten zurückgesetzt werden.
- 1. Deinstallieren Sie die Firewall und wählen Sie bei der Deinstallation die Option, um alle Einstellungen zu löschen.
-
2. Schließen Sie hierfür zunächst die Benutzeroberfläche der Firewall. Anschließend löschen Sie dann das angegebene Verzeichnis. Verzeichnis :
C:/Users/YOUR_NAME/AppData/Roaming/FreeFirewall
